Ambitious security leaders partner with Stratascale to create a culture of security and infuse it into every layer of their enterprise so they can focus on what's next, not what's standing in their way.
We're Helping
Security Leaders...
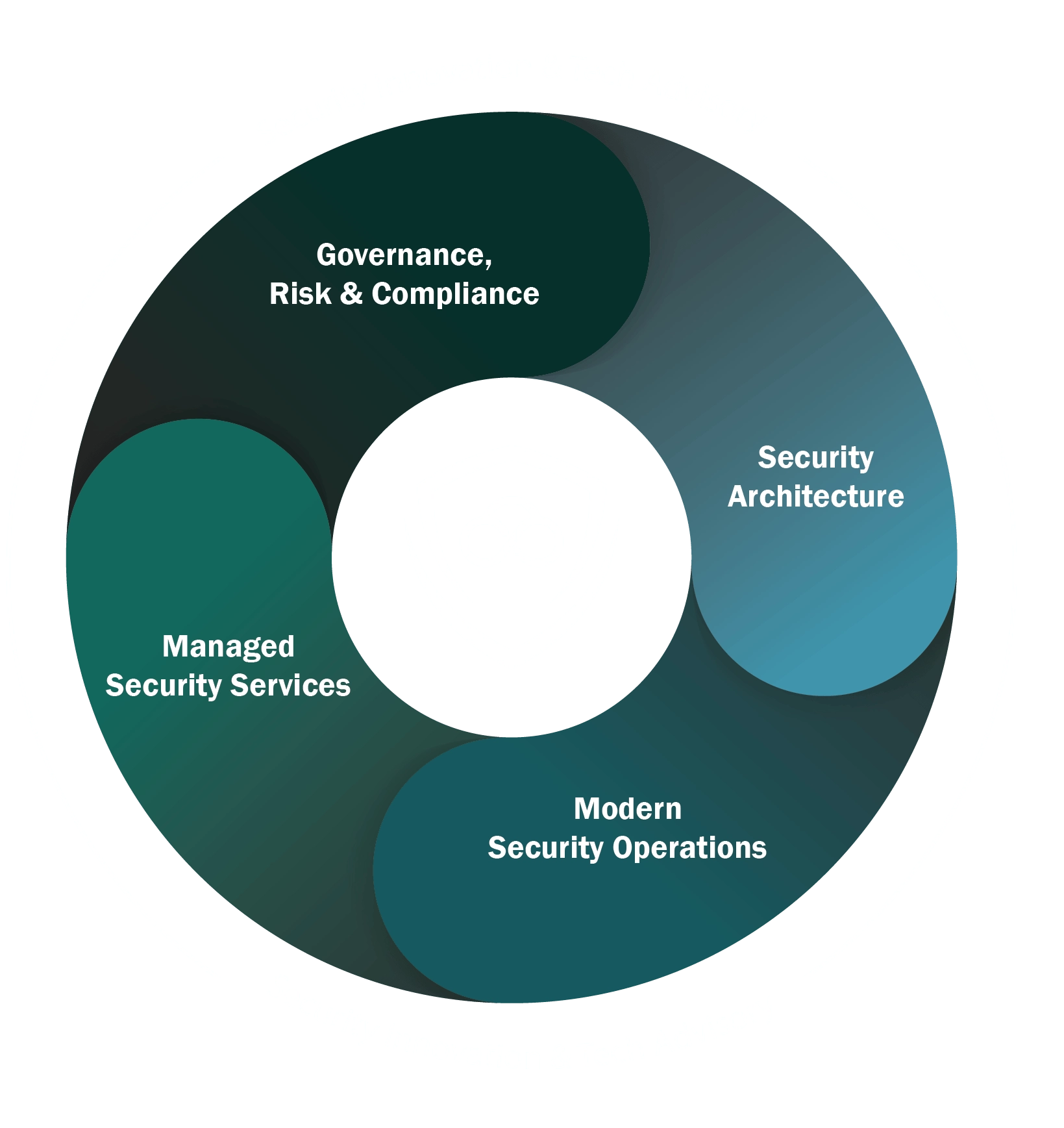
End to End Cybersecurity Services
Integrated Services that Help You Achieve Continuous Security
From pen testing to managed adversarial operations, our services strategically integrate to form robust solutions that solve complex, multi-domain problems and set the stage for modern security operations.
The Best Defense is a Strong Offense
Stratascale Cybersecurity Fusion Center
In today's security landscape, playing defense isn't enough. Reducing risk requires an offensive posture and a trusted partner - one who understands your environment inside and out.
Through our Cybersecurity Fusion Center we combine battletested talent with automation and AI to proactively defend against modern adversaries and deliver the data and attack insights you need to make strategic decisions.
Driving Business Outcomes
We are purpose-built to deliver clear-eyed strategy and game-changing cybersecurity solutions to the Fortune 1000.

Align Security to Business Strategy
Position cyber as a differentiator. Go beyond compliance and siloed solutions by building a holistic security program that strengthens risk posture, fuels growth, and drives competitive edge.

Adopt an
Attacker’s Mindset
Embrace Continuous Threat Exposure Management and supporting security services to outpace modern adversaries and close security gaps before they become mission critical.

Increase
Cyber Resiliency
Shift from an incident-driven mindset and boost organizational confidence and trust by operationalizing your ability to effectively prepare for, respond to, and recover from cyber attacks.

Elevate
Security Operations
Modernize operations by fusing automation with human assistance to minimize attacker dwell time, reduce analyst workload, and deliver continuous protection.

Align Security to Business Strategy
Position cyber as a differentiator. Go beyond compliance and siloed solutions by building a holistic security program that strengthens risk posture, fuels growth, and drives competitive edge.

Adopt an
Attacker’s Mindset
Embrace Continuous Threat Exposure Management and supporting security services to outpace modern adversaries and close security gaps before they become mission critical.

Increase
Cyber Resiliency
Shift from an incident-driven mindset and boost organizational confidence and trust by operationalizing your ability to effectively prepare for, respond to, and recover from cyber attacks.

Elevate
Security Operations
Modernize operations by fusing automation with human assistance to minimize attacker dwell time, reduce analyst workload, and deliver continuous protection.
Contact us today to learn how we can help you
achieve continuous security
Latest Insights
Stratascale Thought Leadership and Practical Advice